Layer 2 – LAN Switching Part – II
Contents
Lan Segmentation using VLAN:
A Virtual Local Area Network (VLAN) is defined as a broadcast domain within a switched network. Broadcast domains describe the extent to which a network propagates a broadcast frame generated by a host. A Broadcast Domain could be a couple of Ports in a switch or it may also span many other switches. Some switches may be configured to support a single or multiple VLANs.
Whenever a switch supports multiple VLANs, broadcasts within one VLAN never appear in another VLAN. Switch ports configured as a member of one VLAN belong to a different broadcast domain, as compared to switch ports configured as members of a different VLAN. There must be a Layer 3 device to get traffic from one VLAN to another. Design wise each VLAN must belong to a separate IP network. This is because, to allow inter-VLAN traffic a router must switch packets between the Broadcast Domains and a Router must not have 2 interfaces in a same IP network.
Advantages of VLANs:
o A group of users needing high security can be put into a VLAN so that no users outside of the VLAN can communicate with them.
o VLANs segment a Broadcast Domain there by increasing the number of broadcast domains while decreasing their size. This allows effective utilization of bandwidth.
o Network adds, moves, and changes are achieved by configuring a port into the appropriate VLAN. This allows logical grouping of users by function, VLANs can be considered independent from their physical or geographic locations.
o To classify traffic by prioritizing them called Quality of Service (QOS)
VLAN Types:
Static VLAN: When a switch port connecting to a host is assigned to a particular VLAN, it is Static VLAN. The administrator must manually assign a host to a particular VLAN. This type of configuration is easy to implement and monitor. This is mostly used in such networks where the movement of users from one VLAN to another is limited.
Dynamic VLAN: When a switch port connecting to a host is assigned automatically, it is Dynamic VLAN. The hosts are assigned to a VLAN dynamically according to their MAC address. For this a database must exist with all the MAC addresses, which then can be used for dynamic assignment of VLANs. A VLAN Management Policy Sever (VMPS) which has the MAC address database is responsible for the dynamic allocation of VLANS.
Identifying VLANs:
In a typical LAN, where there are no VLANS, where there is only one Broadcast Domain; there is no need to identity a frame from a particular host. In that case all the hosts are belonging to a single VLAN or Broadcast Domain. But when a LAN is divided into many VLANS with a single switch, the switch can internally identify a host because it knows to which VLAN a port belongs to.
When A VLAN spans many switches then each switch must be able to identify a frame, from which VLAN it is originated. So there must be a mechanism in the Layer 2 Frame which can identify it uniquely. This is done by Tagging the Frame with its VLAN ID.
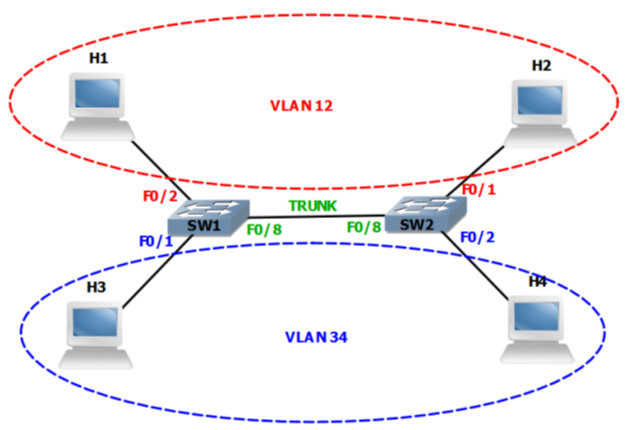
Figure 2.5 LAN segmented using VLANS.
In the figure 2.5 there are two broadcast domains because we have 2 VLANS. In the VLAN 12 there are hosts H1 and H2. But they are on different switches. As I mentioned before there must be a mechanism which can be used to identify the frame from H1 and H2 that it is belonging to the VLAN 12. So the Frame must be tagged with the VLAN ID as it is sent over the link between the switches.
How does VLAN work?
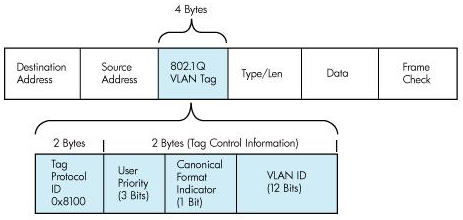
To examine what is happening behind the scenes let us compare a normal Ethernet header and 802.1Q Tag applied Ethernet frame header.
The figure 2.6 is a frame where 802.1Q tag is applied. The tag is inserted between Source MAC Address field and Payload Type field. The 4 byte tag uses the first 2 bytes to mention the Payload Type. The Payload Type field is maintained exactly in the same position as in a normal Ethernet frame. The next 3 bits are for prioritizing the frame. The final 12 bits are used for VLAN ID. So there could be a maximum of 4096 VLANs. When the sending switch adds a tag the CRC will become invalid so it recalculates the CRC.
Let us have a look at the scenario when the H1 pings H2 from figure 2.5.
1. H1 sends an ICMP packet encapsulated frame to SW1.
2. SW1 knows that the port on which the frame came in is assigned to the VLAN 10, and then it checks the MAC table for the exit interface.
3. Then it forwards the frame over the link (Trunk) which is connected to SW2 after inserting a Tag and recalculating the CRC.
4. SW2 receives the frame and finds out that the destination MAC must be in VLAN 10.
5. It then does a MAC table lookup for the exit interface.
6. Before sending the frame to H2 it removes the Tag and recalculates the CRC.
7. Finally the frame is arrived at H2.
8. When H2 sends an ICMP reply the same thing happens
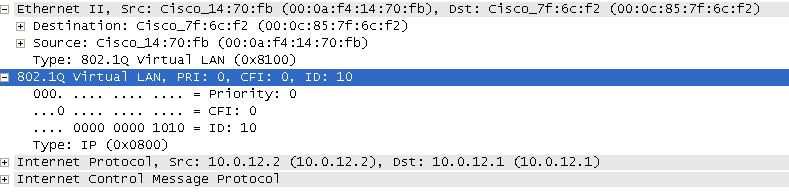
Figure 2.7 Wireshark capture of 802.1Q tag
In the figure 2.7 you can see that the type code for 802.1Q is 8100 and also the VLAN ID is 10.
Switch Port Modes:
There are two types of port modes in a Switched environment. A switch port cannot work in both modes at the same time. They are:
o Access Mode
o Trunk Mode
Access mode:
This is the mode where the port is connected to the end devices. The Access port normally will be connected to hosts printers etc. The tag information is removed before the frame is sent out of an Access port. So the end device does not have any idea about VLANS. A port can belong to only one VLAN. A frame from one VLAN must be passed over a Layer 3 device to enter another VLAN.
Let us check how a VLAN can be created and a port is assigned to it.
SW1(config)#vlan 10 !creating VLAN 10
SW1(config-vlan)#name VLAN_10 !named the VLAN
SW1(config-vlan)#int f0/8 !changing to interface mode
SW1(config-if)#switchport mode access !changing port mode to Access
SW1(config-if)#switchport access vlan 10 !port assigned to VLAN 10
CON output 2.8 Verifying VLANs.
SW1#sh vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/2, Fa0/3, Fa0/4, Fa0/5
Fa0/6, Fa0/7, Fa0/9, Fa0/10
Fa0/11, Fa0/12, Fa0/13, Fa0/14
Fa0/15, Fa0/16, Fa0/17, Fa0/18
Fa0/19, Fa0/20, Fa0/21, Fa0/22
Fa0/23, Fa0/24, Fa0/25, Fa0/26
10 VLAN_10 active Fa0/8
!< output cut >
From the output 2.8 you can see that VLAN 10 is created and named. The port F0/8 is also assigned to VLAN 10. By default all ports belong to VLAN 1. The VLAN1 cannot be deleted. You may also notice that port F0/1 is not in the list. We can discuss of that later.
Now what will happen if the VLAN 10 is deleted? Let us check.
SW1(config)#no vlan 10
CON output 2.9 Verifying existing VLANs.
SW1#sh vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/2, Fa0/3, Fa0/4, Fa0/5
Fa0/6, Fa0/7, Fa0/9, Fa0/10
Fa0/11, Fa0/12, Fa0/13, Fa0/14
Fa0/15, Fa0/16, Fa0/17, Fa0/18
Fa0/19, Fa0/20, Fa0/21, Fa0/22
Fa0/23, Fa0/24, Fa0/25, Fa0/26
!< output cut >
The interface F0/8 is not in the VLAN database. This is because the interface F0/8 was assigned to VLAN 10 and then the VLAN 10 itself is deleted. The port is still a member of VLAN 10.
CON output 2.10 Verifying interface status.
SW1#sh interface f0/8 status Port Name Status Vlan Duplex Speed Type Fa0/8 Link to R1 connected 10 a-full a-100 10/100BaseTX
When a VLAN is deleted, the ports which belong to it will not be reassigned back to the default VLAN 1. So the port will not be listed in the VLAN database. Now what about interface F0/1. Why it is not listed in the VLAN database? It does not show in the database because it is in Trunk mode.
Trunk mode:
In this mode the switch port is usually connected to other switches. Over a Trunk port all the VLANs are transmitted by default. The switch which sends the frame over the Trunk will insert the tag, and then recalculate the CRC of the frame. This enables the receiving switch to identify from which VLAN the frame originated from and is destined to. The tag also enables to multiplex VLANs over a single physical link. All VLANs are transmitted over the trunk port with the default configuration.
As the Trunk port transmits all VLANs this feature can be exploited, like for example a server could be connected over a Trunk port and there by users in different VLANs can access the information without using a Layer 3 device. A Trunk link will be used for the interface which connects to the router which does inter VLAN routing with one physical interface (Router on a Stick).
CON output 2.11 Verifying trunking interfaces.
SW1#sh interface trunk Port Mode Encapsulation Status Native vlan Fa0/1 desirable 802.1q trunking 1 Port Vlans allowed on trunk Fa0/1 1-4094 Port Vlans allowed and active in management domain Fa0/1 1 Port Vlans in spanning tree forwarding state and not pruned Fa0/1 1
In the output 2.11 you can see that port F0/1 is in trunking mode. All VLANs are allowed to pass over the trunk by default. At the moment only the VLAN 1 is active in the switch. This could mean that no other VLANS are configured or is deactivated. The output also shows that the Native VLAN is 1.
Native VLAN
Native VLAN is the VLAN whose frames are not tagged while sent over the trunk. The Native VLAN feature of 802.1Q allows a Switch to also work with a VLAN unaware switch. The VLAN unaware switch can interpret only the frames without 802.1Q tags. The Native VLAN is the VLAN 1 (default) on Cisco Switches by default. As Native VLANs are not tagged QOS cannot be implemented on the frames from the Native VLAN.
When the switch on the other end of the trunk receives a frame that does not have a tag, the frame will be a part of the native VLAN on the receiving switch. Because of this behavior both switches must have the Native VLANs identical. The only difference between a regular VLAN and the native VLAN is that frames from/to the Native VLAN are carried Untagged.
Dynamic Trunking Protocol (DTP)
DTP is a Cisco proprietary layer 2 protocol which is used to dynamically negotiate the status of a port. The port can ultimately be an Access or Trunk. The DTP thus negotiates if it should trunk and which encapsulation to be used for trunking. If both the switches support ISL it will be used otherwise 802.1Q. Most of the switches do not support ISL.
A port can be assigned the mode of operation statically to Access or Trunk. If not then DTP could negotiate the Trunk. The dynamic negotiation depends on the modes configured on the other end of the link. There are two different modes of operation. They are:
o Dynamic auto
o Dynamic desirable
Dynamic auto: In this mode the switch port is passively waiting for a negotiator so that it can form a trunk. A trunk link will only be formed if the other end is set to Trunk (On) or Desirable. As soon as the port hears from the other end it answers. If both ports on the switches are set to auto, they will never form a trunk.
Dynamic desirable: DTP frames are sent out periodically. The local switch port advertises to the remote switch port that it is able to trunk and asks the remote switch port to go to the trunking state. If the local port detects that the remote has been configured as Trunk, desirable or auto mode, it ends up in trunking state.
CON output 2.12 Verifying interfaces switchport characteristics.
SW1#sh interface f0/1 switchport Name: Fa0/1 Switchport: Enabled Administrative Mode: dynamic desirable Operational Mode: trunk Administrative Trunking Encapsulation: dot1q Operational Trunking Encapsulation: dot1q Negotiation of Trunking: On Access Mode VLAN: 1 (default) Trunking Native Mode VLAN: 1 (default) !
Trunking VLANs Enabled: ALL Pruning VLANs Enabled: 2-1001 Capture Mode Disabled Capture VLANs Allowed: ALL Protected: false Appliance trust: none
In the CON output 2.12 you can see the various switch port characteristics. The administrative mode is set to dynamic desirable which is the default setting. The current operation mode is Trunk. The negotiation of Trunking is “On”, that means that the port is participating in DTP. When the switch is not trunking it will be in the VLAN 1 which is also the default setting. The Native VLAN is VLAN 1. This trunk will carry all VLANs which is by default.
For a trunk to be dynamically formed the VTP domain names also have to match if one is set.
Table 2.5 DTP modes and trunk possibilities.
|
Switch port DTP Mode
|
Switch port DTP Mode
|
Dynamic Trunk
|
|
Dynamic auto
|
Dynamic auto
|
NO
|
|
Dynamic auto
|
Dynamic desirable
|
YES
|
|
Dynamic auto
|
ON (configured to Trunk)
|
YES
|
|
Dynamic desirable
|
ON
|
YES
|
A port which is statically configured to trunk is also called “On” mode in DTP. If DTP is turned off then the port must be configured for the mode of operation.
VLAN Trunking Protocol (VTP)
VTP is a Layer 2 protocol used to maintain the VLAN configuration consistency by adding deleting and renaming of VLANs centrally. It is a Cisco proprietary protocol. The concept is to create, delete or manage VLANs only on the VTP server and then the change reflects on the whole VTP domain. This allows the administrator to manage the whole VLAN information just from one switch.
For VTP to operate, the switches must belong to the same VTP management domain. By default there is no VTP domain name. When you configure the domain name on one switch it will send out VTP advertisements out of all trunk ports and then the other receiving switches will have their domain name changed to the one which you configured. The VTP Domain name is case sensitive.
VTP switches use an index called the VTP configuration revision number to keep track of the most recent information. Every switch in a VTP domain stores the configuration revision number that it last heard from a VTP advertisement. The VTP advertisement process always starts with configuration revision number of zero. When subsequent changes are made on a VTP server, the revision number is incremented before the advertisements are sent.
When other switches in the same VTP domain receive an advertisement with a greater revision number than the one locally stored, the advertisement overwrites any stored VLAN information. Because of this, it is very important to always force any newly added network switches to have revision number Zero before being attached to the network. The revision number can be reset by either changing the domain name or changing the VTP mode to Transparent.
Modes of Operation:
There are three different modes of operation within a VTP domain. They are:
o Server
o Client
o Transparent
VTP Server: In Server mode you are able to add, delete and rename VLANs. This switch will then propagate the VLAN information throughout the VTP domain. This is the default mode for switches. The VTP Server is responsible for generating VTP messages. In each VTP domain there must be at least one Server. In this mode the VLAN information is stored in flash as a file called vlan.dat.
VTP Client: In Client mode you cannot manage VLANs. A VTP Client will relay VTP messages which it gets from the Server. The Client must have the same domain name as the server to get its VLAN database updated. A Client may send out its own advertisements when it realizes that it has a greater revision number by receiving an inferior advertisement from the Server. Then, it sends out a subset advertisement with the greater revision number, which VTP Server will accept as more up-to-date information.
VTP Transparent: In Transparent mode you can add, modify and delete VLANs. The VLANS are not advertised. The switch in this mode also does not process VTP advertisements. It relays the advertisements out of its trunk ports. With VTP mode Transparent you effectively turn off VTP for the switch.
CON output 2.13 Verifying VTP status.
SW1#sh vtp status VTP Version : 2 Configuration Revision : 0 Maximum VLANs supported locally : 250 Number of existing VLANs : 5 VTP Operating Mode : Server VTP Domain Name : VTP Pruning Mode : Disabled VTP V2 Mode : Disabled VTP Traps Generation : Disabled MD5 digest : 0xCD 0xD4 0xFE 0xDA 0x7A 0x0C 0x69 0xBD Configuration last modified by 0.0.0.0 at 3-1-93 04:33:58 Local updater ID is 0.0.0.0 (no valid interface found)
In the output 2.13 you can see the VTP mode is Server. The configuration revision number is 0 which means no changes are made to the VLAN database. There is also no domain name configured.
VTP Pruning
VTP pruning makes more efficient use of trunk bandwidth by reducing unnecessary flooded traffic. Broadcast and unknown unicast frames on a VLAN are forwarded over a trunk link only if the switch on the receiving end of the trunk has ports active in that VLAN or if it is in the transit path to other switches which has ports active in a particular VLAN. In other words, VTP pruning allows switches to prevent broadcasts and unknown unicasts from flowing to switches that do not have any ports in that VLAN. By default, VTP pruning is disabled.
Switch Port Security
Port Security is a security feature that remembers the MAC address connected to the switch port and allows only that MAC address to communicate on that port. If any other MAC address tries to communicate through the port, Port Security can disable the port. When port security is activated, the switch will allow only the first MAC address. By default, if any other device is connected the port will be error disabled (shutdown).
The number of MAC address to be allowed can be configured as well as the action to be taken in case of a security violation.
Inter-VLAN Communication:
A VLAN is a broadcast domain. To have communication between broadcast domains we need a Layer 3 device, a Router. The Router will switch the packets between the broadcast domains. I will explain later how a router operates. But for the time now, we will look at the communication flow between hosts in 2 different VLANS.
In a traditional network that uses multiple VLANs to segment the network, routing is performed by connecting different physical router interfaces to different physical switch ports. The switch ports connected to the router are in access mode.
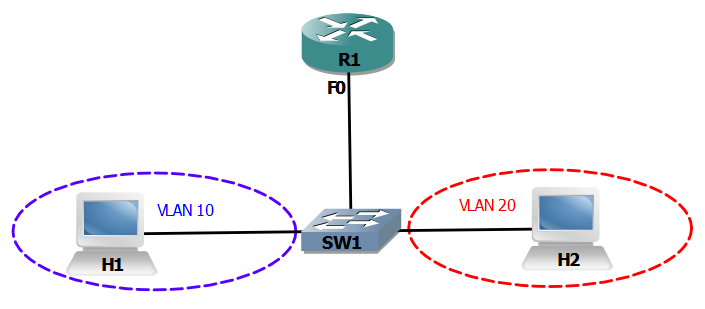
Figure 2.8 Traditional Inter-VLAN routing
The router R1 in figure 2.8 which does the Inter-VLAN routing has 2 physical interfaces. One of its interfaces is assigned to VLAN 10 and the other assigned to VLAN 20. The host H1 is has its Gateway address as the IP address of F0 interface from router R1. Thus when the host H1 wants to send a packet to host H2 it contacts the router, which then routes the packet out of the F1 interface.
Traditional Inter-VLAN routing requires multiple physical interfaces on both the router and the switch. Router-on-a-stick is a type of router configuration in which a single physical interface routes traffic between multiple VLANs on a network.
Figure 2.9 Router-on-a-Stick Inter-VLAN routing
In the figure 2.9 the router interface is configured to operate as a trunk link and is connected to a switch port which is configured in trunk mode. The router performs the inter-VLAN routing by accepting VLAN tagged traffic on the trunk interface and internally routing between the VLANs using Sub-Interfaces. The router then forwards the traffic with the appropriate TAG for the destination VLAN out the same physical interface.
Sub-Interfaces are Virtual Interfaces which are associated with one physical interface. These Sub-Interfaces are configured in software on a router that can be configured with an IP address and appropriate VLAN assignment to operate on a specific VLAN. Sub-Interfaces are configured for different IP networks corresponding to their VLAN assignments to facilitate routing. Then the data frames are VLAN tagged and sent back out of the same physical interface.
Now let’s get to the CLI and check the configuration. The following tasks must be done:
1. Configure the interface of SW1 connecting to R1 as a trunk.
2. Create and Configure Sub-Interfaces on R1.
3. Assign appropriate VLAN tag for the Sub-Interfaces.
4. Assign IP address for Sub-Interfaces which the hosts will use as their gateways.
SW1(config)#interface f0/8
SW1(config-if)#switchport mode trunk ! Configured interface f0/8 to trunk mode
R1(config)#interface f0
R1(config-if)#no shutdown
R1(config-if)#interface f0.10 ! Created Sub-Interface numbered 10
R1(config-subif)#encapsulation dot1Q 10 ! Assigned the VLAN tag of 10
R1(config-subif)#ip address 10.0.0.1 255.0.0.0 ! Assigned an IP address
R1(config-subif)#interface f0.20 ! Created Sub-Interface numbered 10
R1(config-subif)#encapsulation dot1Q 20 ! Assigned the VLAN tag of 10
R1(config-subif)#ip address 20.0.0.1 255.0.0.0 ! Assigned an IP address
After this configuration on switch and router, the hosts must be assigned with the IP address of the router as their gateway. Host H1 will be assigned as 10.0.0.1 as its Gateway and host H2 will be assigned 20.0.0.1 as its Gateway.
Command Reference:
Table 2.6 VLAN configuration and monitoring commands
|
Global config mode
SW1(config)# |
Purpose
|
|
vlan 10
|
Creates VLAN 10
|
|
vlan config mode
SW1(config-vlan)# |
Purpose
|
|
name VLAN_10
|
Named the VLAN 10 to VLAN_10
|
|
Shutdown
|
Deactivate the VLAN 10
|
|
interface config mode
SW1(config-if)# |
Purpose
|
|
switchport mode access
|
Configured for access mode
|
|
switchport mode trunk
|
Configured for trunk mode
|
|
switchport mode dynamic auto
|
Configured for passive negotiation of trunk
|
|
switchport mode dynamic desirable
|
Configured for active negotiation of trunk
|
|
switchport access vlan 10
|
Vlan 10 will be created if it does not exist and the port will be in vlan 10 if it is in access mode
|
|
switchport trunk allowed vlan 10
|
Only VLAN 10 will be allowed over the trunk
|
|
switchport trunk allowed vlan except 10
|
Only disallows VLAN 10 over the trunk
|
|
switchport trunk allowed vlan remove 10
|
Only removes VLAN 10 from the trunk
|
|
switchport nonegotiate
|
Turns of DTP
|
|
switchport trunk native vlan 10
|
Sets Native VLAN to 10
|
|
Enable mode
SW1# |
Purpose
|
|
sh vlan brief
|
Display the VLAN and port mappings
|
|
sh interface trunk
|
Display the trunk ports and allowed vlans
|
|
sh interface switchport
|
Displays the switchport characteristics
|
|
Sh int f0/1 switchport
|
Displays the switchport characteristics from f0/1
|
Table 2.7 VTP configuration and monitoring commands
|
Global config mode
SW1(config)# |
Purpose
|
|
Vtp mode <server> <client> <transparent>
|
Sets the VTP mode
|
|
vtp domain lab
|
Sets the VTP domain name to “lab”
|
|
vtp pruning
|
Enables pruning in the VTP domain
|
|
sh vtp status
|
Shows the VTP configuration revision number and mode of operation domain name etc.
|
Table 2.8 Port security configuration and monitoring commands
|
interface config mode
SW1(config-if)# |
Purpose
|
|
switchport port-security
|
Activates port security with default settings
|
|
switchport port-security maximum 10
|
Sets the maximum allowed MAC address to 10
|
|
Enable mode
SW1# |
Purpose
|
|
sh port-security
|
Displays the security status
|
|
Sh port-security interface f0/8
|
Displays the detailed status from interface f0/8
|
|
clear port-security dynamic
|
Clears all dynamically learned addresses
|