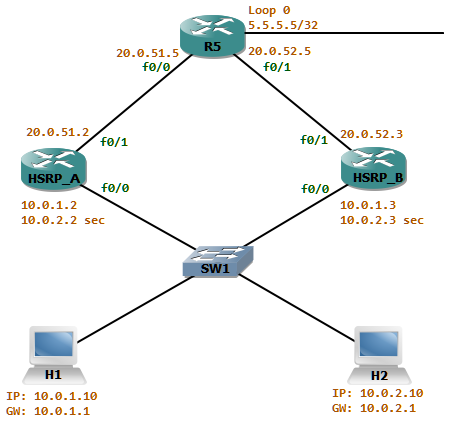
Initially there were about 250 hosts in the network attached to switch SW1. The Gateway router HSRP_A is the active router for the network. As the number of hosts increased in the network attached to SW1, a new subnet (10.0.2/24) is introduced as a secondary address in the gateway routers. To achieve some load sharing HSRP_B will be the active router for the group 1 for the network 10.0.1/24 and HSRP_A active for the group 2 which is the 10.0.2/24 network.
The ospf cost advertised from HSRP_A is better than the one advertised from HSRP_B. Thus the return traffic from the network attached to R5 will always take the path via HSRP_A. now let’s look at this scenario where some traffic filtering is in place.
HSRP_A has a filtering rule which states only to allow inbound TCP sessions if it was originated from the networks attached to SW1. For this HSRP_A has an outbound access-list attached to f0/1 named OUTBOUND_ACL_OUT which reflects the outgoing tcp sessions to a reflexive access-list named TCP.