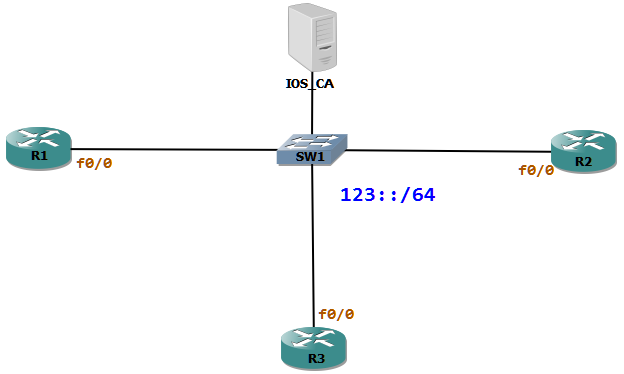
R1 will be advertising the 123::/64 prefix to the local LAN. R2 and R3 are hosts which will generate IPv6 address from the Router Advertisement (RA).
IPv6 hosts in the same broadcast domain use Neighbor Discovery Protocol (NDP) to find out the data link layer address of others. The functions of NDP are Neighbor Discovery, Router Discovery, Address Auto configuration, Address Resolution, Neighbor Unreachability Detection, Duplicate Address Detection, and Redirection. The NDP same as ARP does not have any mechanism to prevent masquerading attacks.
We can use Secure Neighbor Discovery (SeND) to protect against such attacks. SeND uses a RSA key pair along with other parameters to generate an IPv6 address which is called Cryptographically Generated Address (CGA).
The Router Advertisements are so crucial, in IPv6 deployments for stateless auto configuration. But as there is not implied security in the ND protocols we could use SeND to protect those. The basic idea is to introduce a third party who trusts the identity of the router who is supposed to send the advertisements. When a router sends a RA, the receiving node asks to the router an identity certificate. When the client receives the identity certificate of the router, it checks for the certificates authenticity.
To achieve this 2 new ICMP types are defined, Certification Path Solicitation (CPS message type 148) and Certification Path Advertisement (CPA message type 149). CPS messages are sent from the nodes to routers asking for their identity. CPA messages are sent by the routers which contains the digital certificate of the router.
First Let us configure R1 to be an IPv6 router which will then serve prefixes to the others for auto-configuration using SeND. R2 and R3 are hosts which generate address using CGA.
We must do the following tasks to configure the router for SeND
- Generate a RSA key pair.
- Get this RSA key signed from a trusted CA.
- The Prefix which the router advertises must be included in the certificate.
- Generate a CGA modifier from the RSA key.
- Link local address must be cryptographically generated.
Step 1 Generation of RSA keys and getting it signed from the IOS_CA with prefix.
First we can generate a RSA key pair with the name SEND. Then we must get this key signed from a Certificate Authority, in our case IOS_CA.
R1(config)#crypto key generate rsa label SEND modulus 1024The name for the keys will be: SEND% The key modulus size is 1024 bits% Generating 1024 bit RSA keys, keys will be non-exportable...[OK]Now we must get a certificate from a trusted CA. This certificate will have the public key of R1 be digitally signed with the private key of IOS_CA. The issued certificate from IOS_CA must also include the prefix which R1 advertises via RA. To achieve this we have to create a trust point (TP) and get this TP enrolled from the IOS_CA.
R1(config)#crypto pki trustpoint SENDR1(ca-trustpoint)#enrollment url http://10.0.0.100R1(ca-trustpoint)#ip-extension prefix 123::/64R1(ca-trustpoint)#rsakeypair SENDR1(config)#crypto pki authenticate SENDCertificate has the following attributes: Fingerprint MD5: 19AEB2D2 B69DDF84 02B5F4F5 8A8E32FA Fingerprint SHA1: 84A55044 22E4864F A283502D 2DAC9963 E7674D15% Do you accept this certificate? [yes/no]: yesTrustpoint CA certificate accepted.R1(config)#crypto pki enroll SEND%% Start certificate enrollment ..% Create a challenge password. You will need to verbally provide this password to the CA Administrator in order to revoke your certificate. For security reasons your password will not be saved in the configuration. Please make a note of it.Password:Re-enter password:% The subject name in the certificate will include: R1% Include the router serial number in the subject name? [yes/no]: no% Include an IP address in the subject name? [no]:Request certificate from CA? [yes/no]: yes% Certificate request sent to Certificate Authority% The 'show crypto pki certificate verbose SEND' commandwill show the fingerprint.*Oct 7 11:12:44.475: CRYPTO_PKI: Certificate Request Fingerprint MD5: 8EA9BFAF 1AB216C2 04E0DF2A 932065C9*Oct 7 11:12:44.479: CRYPTO_PKI: Certificate Request Fingerprint SHA1: 47B22B52 D8064355 1B10416B B9E9F2C4 81E6AC0D*Oct 7 11:12:45.091: %PKI-6-CERTRET: Certificate received from Certificate Authority
At this point we must have a certificate issued from the CA with the prefix approved to advertise.
R1#sh crypto pki certificates verboseCertificate Status: Available Version: 3 Certificate Serial Number (hex): 02 Certificate Usage: General Purpose Issuer: cn=CA Subject: Name: R1 hostname=R1 Validity Date: start date: 11:12:44 UTC Oct 7 2012 end date: 11:12:44 UTC Oct 7 2013 Subject Key Info: Public Key Algorithm: rsaEncryption RSA Public Key: (1024 bit) Signature Algorithm: MD5 with RSA Encryption Fingerprint MD5: D5549E4C 8F01C5CE 0DE91439 68814DBE Fingerprint SHA1: EDA7D1B2 44E25146 09EF0690 B20CC1F6 B8A33A77 X509v3 extensions: X509v3 Key Usage: A0000000 Digital Signature Key Encipherment X509v3 Subject Key ID: A4ADD94A 41E0458C AE522B3B 12B1DE1F 6E7A75A0 X509v3 Authority Key ID: 460E67A9 7BE6D8A3 62064B57 1ADA2712 F6BE9EFF Authority Info Access: X509v3 IP Extension: IPv6: 123::/64 Associated Trustpoints: SEND Key Label: SENDCA Certificate Status: Available Version: 3 Certificate Serial Number (hex): 01 Certificate Usage: Signature Issuer: cn=CA Subject: cn=CA Validity Date: start date: 11:10:12 UTC Oct 7 2012 end date: 11:10:12 UTC Oct 7 2015 Subject Key Info: Public Key Algorithm: rsaEncryption RSA Public Key: (1024 bit) Signature Algorithm: MD5 with RSA Encryption Fingerprint MD5: 19AEB2D2 B69DDF84 02B5F4F5 8A8E32FA Fingerprint SHA1: 84A55044 22E4864F A283502D 2DAC9963 E7674D15 X509v3 extensions: X509v3 Key Usage: 86000000 Digital Signature Key Cert Sign CRL Signature X509v3 Subject Key ID: 460E67A9 7BE6D8A3 62064B57 1ADA2712 F6BE9EFF X509v3 Basic Constraints: CA: TRUE X509v3 Authority Key ID: 460E67A9 7BE6D8A3 62064B57 1ADA2712 F6BE9EFF Authority Info Access: X509v3 IP Extension: IPv6: 123::/32 Associated Trustpoints: SEND
The issued certificate has the prefix which will be advertised by R1. The IOS_CAs certificate has the prefix of 123::/32. Thus R1 is capable of requesting of any prefix which falls in this range.
Step 2 Generation of CGA modifier.
Now we have to generate a modifier for CGA. This modifier is based on the RSA key pair previously generated.
R1(config)#ipv6 cga modifier rsakeypair SEND sec-level 1R1#sh ipv6 cga modifier-db 9304:80:3AB9:F9AB:5FF4:1447:E080:C295 label: SEND sec level: 1 Addresses:Step 3 Activating Cryptographically Generated Link Local Address.
The RA will be sent using the Link Local address. Thus the LLAddress must be CGA. For this we must first generate a CGA modifier.
R1(config)#ipv6 cga modifier rsakeypair SEND sec-level 1R1#sh ipv6 cga modifier-db 9304:80:3AB9:F9AB:5FF4:1447:E080:C295 label: SEND sec level: 1 Addresses:
As the CGA modifier is generated we can now configure the interface to use this modifier. Then we can also generate a Link Local CGA for the interface.
R1(config)#interface f0/0R1(config-if)#ipv6 cga rsakeypair SENDR1(config-if)#ipv6 address fea1:1111:1111:1111:: link-local cga R1#sh ipv6 cga address-db FEA1:1111:1111:1111::/64 ::28A3:A230:DAEF:5FB1 - table 0x12000004 interface: FastEthernet0/0 (4) modifier: SEND collisions: 0
Finally we can advertise the prefix via RA.
R1(config)#interface f0/0R1(config-if)#ipv6 nd prefix 123::/64 R1#sh ipv int f0/0 prefix IPv6 Prefix Advertisements FastEthernet0/0Codes: A - Address, P - Prefix-Advertisement, O - Pool U - Per-user prefix, D - Default N - Not advertised, C - CalendarPD default [LA] Valid lifetime 2592000, preferred lifetime 604800PD 123::/64 [LA] Valid lifetime 2592000, preferred lifetime 604800R1#sh ipv6 interface f0/0FastEthernet0/0 is up, line protocol is up IPv6 is enabled, link-local address is FEA1:1111:1111:1111:28A3:A230:DAEF:5FB1 No Virtual link-local address(es): No global unicast address is configured Joined group address(es): FF02::1 FF02::2 FF02::1:FFEF:5FB1 MTU is 1500 bytes ICMP error messages limited to one every 100 milliseconds ICMP redirects are enabled ICMP unreachables are sent ND DAD is enabled, number of DAD attempts: 1 ND reachable time is 30000 milliseconds (using 35115) ND advertised reachable time is 0 (unspecified) ND advertised retransmit interval is 0 (unspecified) ND router advertisements are sent every 200 seconds ND router advertisements live for 1800 seconds ND advertised default router preference is Medium Hosts use stateless autoconfig for addresses.At this point we are finished with the Router configuration. R2 and R3 are the hosts which will auto generate secure IPv6 address from the RA.
To accomplish this we have to commit the following tasks.
- Generate a RSA key pair.
- Get the CA certificate.
- Generate CGA modifier.
- Activate interfaces for automatic address generation using CGA.
Step 1 Generation of RSA key pairs and download IOS_CA certificate.
First we generate a RSA key pair with the name SEND.
R2(config)#crypto key generate rsa modulus 1024 label SENDThe name for the keys will be: SEND% The key modulus size is 1024 bits% Generating 1024 bit RSA keys, keys will be non-exportable...[OK]Now we can create a trust point as it is needed to download the CA certificate.
R2(config)#crypto pki trustpoint SENDR2(ca-trustpoint)# revocation-check noneR2(ca-trustpoint)#enrollment url http://10.0.0.100R2(config)#crypto pki authenticate SENDCertificate has the following attributes: Fingerprint MD5: 19AEB2D2 B69DDF84 02B5F4F5 8A8E32FA Fingerprint SHA1: 84A55044 22E4864F A283502D 2DAC9963 E7674D15% Do you accept this certificate? [yes/no]: yesTrustpoint CA certificate accepted.R2#sh crypto pki certificates verbose CA Certificate Status: Available Version: 3 Certificate Serial Number (hex): 01 Certificate Usage: Signature Issuer: cn=CA Subject: cn=CA Validity Date: start date: 11:10:12 UTC Oct 7 2012 end date: 11:10:12 UTC Oct 7 2015 Subject Key Info: Public Key Algorithm: rsaEncryption RSA Public Key: (1024 bit) Signature Algorithm: MD5 with RSA Encryption Fingerprint MD5: 19AEB2D2 B69DDF84 02B5F4F5 8A8E32FA Fingerprint SHA1: 84A55044 22E4864F A283502D 2DAC9963 E7674D15 X509v3 extensions: X509v3 Key Usage: 86000000 Digital Signature Key Cert Sign CRL Signature X509v3 Subject Key ID: 460E67A9 7BE6D8A3 62064B57 1ADA2712 F6BE9EFF X509v3 Basic Constraints: CA: TRUE X509v3 Authority Key ID: 460E67A9 7BE6D8A3 62064B57 1ADA2712 F6BE9EFF Authority Info Access: X509v3 IP Extension: IPv6: 123::/32 Associated Trustpoints: SENDStep 2 Generation of CGA modifier and activating SeND on interfaces.
R2(config)#ipv6 cga modifier rsakeypair SEND sec-level 1R2(config)#interface f0/0R2(config-if)#ipv6 cga rsakeypair SENDR2(config-if)#ipv6 address autoconfig*Oct 7 15:30:34.674: SEND: Receive: ND_ROUTER_ADVERT
*Oct 7 15:30:34.678: SEND: src FEA1:1111:1111:1111:28A3:A230:DAEF:5FB1
*Oct 7 15:30:34.682: SEND: dst FF02::1
*Oct 7 15:30:34.682: SEND: Received at: 0x5071A01AAED5 = 15:30:34 UTC Oct 7 2012
*Oct 7 15:30:34.686: SEND: option 1 len 8: ND_OPT_SOURCE_LINKADDR
*Oct 7 15:30:34.686: SEND: option 5 len 8: ND_OPT_MTU
*Oct 7 15:30:34.690: SEND: option 3 len 32: ND_OPT_PREFIX_INFORMATION
*Oct 7 15:30:34.690: SEND: option 11 len 192: ND_OPT_CGA
*Oct 7 15:30:34.694: SEND: option 13 len 16: ND_OPT_TIMESTAMP
*Oct 7 15:30:34.694: SEND: option 12 len 152: ND_OPT_RSA
*Oct 7 15:30:34.698: SEND: Verifying address FEA1:1111:1111:1111:28A3:A230:DAEF:5FB1
*Oct 7 15:30:34.698: SEND: sec is 1
*Oct 7 15:30:34.706: SEND: keylen is 1024
*Oct 7 15:30:34.706: SEND: Address verified
*Oct 7 15:30:34.710: SEND: Timestamp: 0x5071A01A748E = 15:30:34 UTC Oct 7 2012
*Oct 7 15:30:34.710: SEND: TS opt check RC = 0
*Oct 7 15:30:34.718: SEND: Good signature
*Oct 7 15:30:34.722: SEND: RA with prefix option 123::
*Oct 7 15:30:34.722: SEND: Send : CPS
*Oct 7 15:30:34.726: SEND: adding trustanchor cn=CA
*Oct 7 15:30:34.726: SEND: option 15 len 24: ND_OPT_TRUST_ANCHOR
*Oct 7 15:30:34.738: SEND: Receive: ND_CERTIFICATE_ADVERT
*Oct 7 15:30:34.742: SEND: src FEA1:1111:1111:1111:28A3:A230:DAEF:5FB1
*Oct 7 15:30:34.746: SEND: dst FF02::1:FFC0:8
*Oct 7 15:30:34.746: SEND: Received at: 0x5071A01ABF39 = 15:30:34 UTC Oct 7 2012
*Oct 7 15:30:34.750: SEND: option 15 len 24: ND_OPT_TRUST_ANCHOR
*Oct 7 15:30:34.750: SEND: option 16 len 536: ND_OPT_CERTIFICATER2#sh ipv6 interface f0/0
FastEthernet0/0 is up, line protocol is up
IPv6 is enabled, link-local address is FE80::C802:2AFF:FEC0:8
No Virtual link-local address(es):
Stateless address autoconfig enabled
Global unicast address(es):
123::20D2:843E:E9A6:FE13, subnet is 123::/64 [CAL/PRE]
valid lifetime 2591841 preferred lifetime 604641
Joined group address(es):
FF02::1
FF02::1:FFA6:FE13
FF02::1:FFC0:8
MTU is 1500 bytes
ICMP error messages limited to one every 100 milliseconds
ICMP redirects are enabled
ICMP unreachables are sent
ND DAD is enabled, number of DAD attempts: 1
ND reachable time is 30000 milliseconds (using 35611)
Default router is FEA1:1111:1111:1111:28A3:A230:DAEF:5FB1 on FastEthernet0/0
R2#sh ipv6 cga address-db
123::/64 ::20D2:843E:E9A6:FE13 - table 0x0
interface: FastEthernet0/0 (4)
modifier: SEND
collisions: 0