Introduction to Digital Data Network
Contents
Introduction to Network:
Network is a collection of computer devices connected each other for the need of communication. The aim of networks is to get data from one point to another in the most effective manner possible. The network may consist of just 2 Hosts or it may be the Internet where there are thousands of devices interconnected like a web and may be connected over various diverse physical mediums.
What is Protocol?
By definition Protocol is “a formal set of rules and conventions that governs how computers or addressed devices exchange information over a given medium”.
Like human beings interact each other with the help of a language, so do the computer devices. So a Protocol could be thought like a language which is used between two computers. Both of the computers must be able to understand the protocol for a successful communication. An example of protocol is Internet Protocol (IP).
A Protocol has several attributes, like for example the IP Protocol has an Attribute called TTL. This attribute must be also understood by the sending and receiving computers. If one of a computer cannot interpret the attribute TTL, then that computer does not recognize the IP Protocol.
Each Protocol Attributes have Values. For example the TTL Attribute in IP Protocol could be assigned a Value between 0 and 255. All of these Protocol Attribute Values are stored in the Header of the Protocol.
Basic Network Terminology:
Before we discuss further we have to look at the following terms:
Header: A Header could be compared to the address which we write on a letter. It is the address which is written on the letter responsible for its delivery to the recipient. The same way the Header of a Protocol is responsible for helping the devices on the transit path to handle the date appropriately.
Data: Data could be compared to the message of the letter. The Data is the actual information which must be transmitted over a medium, which is then received by the recipient. The data is also referred as Payload.
Trailer: Some protocols use to store values after the Payload. This portion which is not the Header and the Payload is the Trailer.
Protocol Data Unit (PDU): The Protocol Attributes are stored in the Header of the Protocol. The Header along with the Payload and the Trailer is called a PDU. The PDU begins with the Header, then the Payload and finally the Trailer. The PDUs are sometimes also referred as Datagrams.
OSI model:
A model for data transversal had to be invented, because as the need for communication grew, the network grew along with. So there came many manufacturers who produced various hardware and software. Thus the need arose to standardize the procedure of software and hardware development. This lead to the development of the Open Systems Interconnection (OSI) model by the International Organization for Standardization (ISO) in 1984, and it is now considered the primary architectural model for inter-computer communications.
The OSI model consists of 7 layers:
Layer 1 Physical: This is the first layer of the OSI. It’s there to transfer the electric signals from point A to B. The PDUs exchanged are called bits. The devices which operate at this Layer are Network cables, Network Interface Cards, hubs, modems etc.
Layer 2 Data link: This Layer 2 of the model starts with addressing the “Point of Presence” (existence) of a device. Layer 2 is also responsible for error detection. Each sending device determines a Hash Value for the contents of the Frame. It inserts this Value in the Trailer of the Frame. The receiver does the same mathematical computation to retrieve a hash value for the data of the Frame. Then it compares the computed value with the value written in the Trailer. If they match, then the data is assumed error free.
The addressing scheme used is the Media Access Control addresses (MAC) in Ethernet and Data Link Connection Identifier addresses (DLCI) in Frame-Relay. The PDUs area called Frames. The devices which operate at Layer 2 are Switches, Bridges, Wireless Access Points etc. Address Resolution Protocol (ARP), Spanning Tree Protocol (STP), Ethernet, Layer 2 load sharing protocols, WAN protocols area examples of protocols which belong to data link layer.
Layer 3 Network: The Layer 3 of the OSI model is responsible for the logical grouping of Hosts with IP address. The main responsibility of this layer is to take data from one network to another. The addressing scheme used is the IPv4 and IPv6.
The devices that operate at Layer 3 are Routers. All the routing protocols, Internet Protocol (IP), Internet Control Messaging Protocol (ICMP) etc. operate at this layer. The Layer 3 PDUs are called Packets.
Layer 4 Transport: The transport layer accepts data from the Session layer and segments the data for transport across the network. Generally, the transport layer is responsible for making sure that the data is delivered error-free and in the proper sequence. Flow control generally occurs at the transport layer. Flow control manages data transmission between devices so that the transmitting device does not send more data than the receiving device can process and thereby avoiding congestion. Multiplexing which is the most important function of Transport later enables data from several applications to be transmitted onto a single physical link. For this Virtual circuits (sockets) are established, maintained, and terminated by the transport layer.
The transport protocols used on the Internet are TCP and UDP. The Layer 4 PDUs are called Segments.
Layer 5 Session: The Session Layer handles the construction and teardown of the connection between the two end points involved in the communication. This layer works as a mediator between the higher layers and the lower layers.
Layer 6 Presentation: The Presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. For example, a PC program communicates with another computer, one using extended binary coded decimal interchange code (EBCDIC) and the other using ASCII to represent the same characters. If necessary, the presentation layer might be able to translate between multiple data formats by using a common format.
Layer 7 Application: The application layer is the OSI layer that is closest to the user. This layer provides network services to the user’s applications. It differs from the other layers in that it does not provide services to any other OSI layer, but only to applications outside the OSI reference model.
Data Transmission Process:
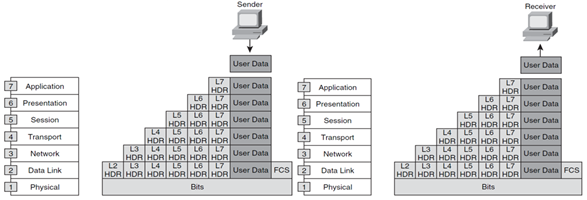
When an end user sends an email the data goes through all the seven layers of the OSI model. The data is broken up into smaller and smaller parts which begin at Layer 4 until it is transformed to Bits, which are then transmitted over the Layer 1 medium.
When the Transport layer receives the data from the upper layers, it places this data inside Segments and adds a Layer 4 header. Then these Segments are passed down to the Network layer where they are placed into Packets and L3 headers are added. Further the Packet is given to the Data Link Layer where the Packet is placed in between Layer 2 header and Layer 2 trailer. Then finally these Frames take the form of Bits in the Physical Layer. This whole process of packing the data in each layer is called Encapsulation Process.
As data flows down the OSI model, each layer adds a header that will be removed by the same layer from the receiving host. The receiving host handles the Frames to the Data Link Layer. Then the L2 will remove the header and trailer and pass the Packet to Layer 3. Network Layer then removes its header and passes the Segment to the Transport Layer. This process is called De-Encapsulation.
Figure 1.1 Encapsulation and De-Encapsulation.
This is called the same-layer interaction process of the OSI. A given OSI Layer removing the header placed on the data by the same layer from the sending side. For example the Date Link Layer will only remove the header and trailer placed by the Layer 2 from the sending side and so forth.
Ethernet:
Ethernet is the most common type of LAN. It was originally developed in the 1970s by Digital Equipment Corporation (DEC), Intel, and Xerox and was called DIX Ethernet. It transmitted data at 10 megabits per second (Mbps). The standard for Ethernet was updated in the 1980s to add more capability, and the new version of Ethernet was referred to as Ethernet II.
Ethernet is a data transmission method where all devices on the network share the link’s bandwidth equally. Thus collisions are part of the operation of Ethernet, occurring when two stations attempt to communicate at the same time.
Data Transmission in Ethernet:
As Ethernet shares a shared medium, it utilizes Carrier Sense Multiple Access with Collision Detection (CSMA/CD). CSMA/CD was created to overcome the problem of those collisions that occur when data is transmitted simultaneously from different hosts. When a host wants to transmit over the network, it first checks for the presence of a digital signal on the wire. If all is clear (no other host is transmitting), the host will then proceed with its transmission. The transmitting host constantly monitors the wire to make sure no other hosts begin transmitting. If the host detects another signal on the wire, it sends out an extended jam signal that causes all hosts on the segment to stop sending data. The hosts respond to that jam signal by waiting a while before attempting to transmit again. Backoff algorithms determine when the colliding stations can retransmit. If collisions keep occurring after 15 tries, the hosts attempting to transmit will then time out.
Collision Domain:
A collision domain is a collection of networking devices in which one particular device sends a packet on a network segment, forcing every other device on that same segment to pay attention to it. For example when H1 H2 and H3 are connected to a hub and when H1 sends a packet to H2, H3 can see that because it’s in the same Collision Domain. A switch segments a Collision Domain. Each Switch Port is a single Collision Domain.
Half-Duplex and Full-Duplex:
Half-duplex Ethernet connections contain one set of wires, basically meaning that a device can transmit or receive, but cannot do both at the same time. Half-duplex uses the CSMA/CD of transmitting data that was defined at the beginning of this section.
A 10Mbps (megabits per second) half-duplex port sounds like it would allow 10Mbps, but in reality, it will not. The inability to send and transmit data simultaneously inherently slows connection speed down, and the nature of CSMA/CD means that an Ethernet port will be told on occasion that it cannot transmit.
Full-duplex Ethernet contains two set of wires, allowing devices to transmit and receive simultaneously. Since the incoming data is traveling on a different set of wires than the outgoing data, there are no collisions. Theoretically, on a 100 Mbps full-duplex connection, the port should be able to transmit at 100 Mbps and send at 100 Mbps for an overall transmission of 200 Mbps. Half-duplex Ethernet shares a collision domain and there by provides a lower effective throughput than full-duplex Ethernet.
Cabling Types:
Devices on an Ethernet network are connected by either a straight-through cable or a crossover cable. The straight-through cable describes the physical connectivity of the wires inside the cable. A router will use a straight-through cable to connect to a hub or switch. The crossover cable has wires that crosses over between pins. A crossover cable is used for the following connections: switch-switch, hub-hub, host-host, switch-hub, or if a router is connected directly to a host. There is a third type of cable, a rollover cable. It’s similar to a crossover cable, but eight wires are used instead of four. The important factor is that a rollover cable makes it possible for a host to connect directly to the Console port of a router.
A cross cable is always used to connect two same devices. Exceptions are Router to PC and Switch to Hub.
Broadcast Domain:
In digital networks a communication could be Unicast, Multicast or Broadcast. To understand this concept, let us assume that we have 9 hosts in a class room which communicate.
Unicast: It is the communication which occurs between two devices. For example host H1 communicating only with H2. Thus we can tell that H1 is unicasting to H2.
Multicast: It is the communication which occurs from one device to a couple of devices. For example host H1 communicates with a 3 hosts in the class room. Only this 3 hosts or group of hosts receives the communication from the total number of 9 hosts.
Broadcast: This is the communication which occurs from one host to all devices. When host H1 sends a broadcast packet everyone receives this. A broadcast is heard by everyone in the class room.
Now with this understanding we could define the very most important concept of networking; the BROADCAST DOMAIN. Imagine that the class room has just one door to get outside and there are 9 persons (hosts) in the room. If one person shouts (broadcasts) everyone hears. So this is the key to define a Broadcast Domain. The terms Network, a Virtual Local Area Network (VLAN), IP Network etc. refer to a Broadcast Domain.
Technically speaking “A layer 3 device should not relay broadcasts” thus Router being a layer 3 device stops relying broadcasts. Thus it defines the border to a given Broadcast Domain.
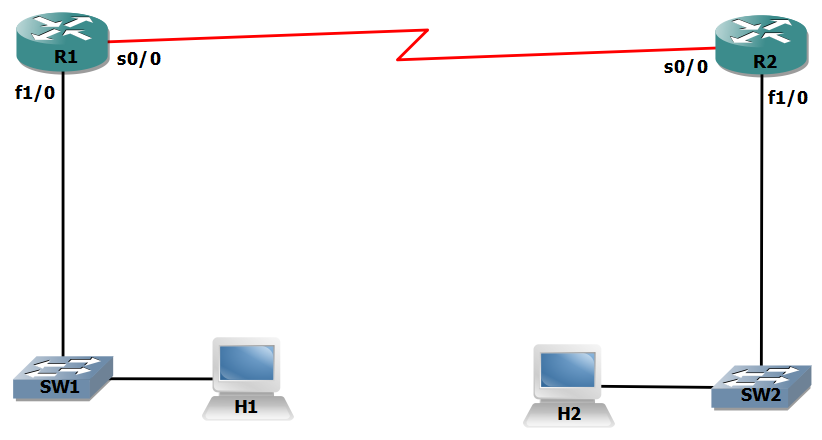
Figure 1.2 Defining Broadcast Domains.
In the topology in figure 1.2, we have 2 Routers (R1 and R2) connected to Switch SW1 and SW2. In this case as you think we have 3 Broadcast Domains. In case if host H1 sends a broadcast the Switch SW1 relays the frame to Router R1. The f1/0 interface from Router R1 receives the frame but does not relay it anymore further. So the Router R1 is the border to the Broadcast Domain from the perspective of host H1. Again there is another Broadcast Domain between Router R1 and R2 and between Router R2 and H2.
A layer 3 device stops forwarding of broadcasts and thus they define the end to a broadcast domain. It’s very important to understand the term Broadcast Domain to de-mystify the complexities of networking.
Communication between hosts in the same Broadcast Domain:
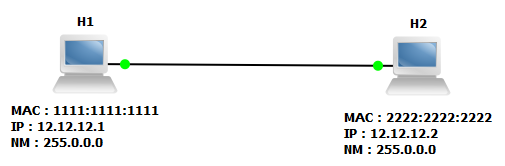
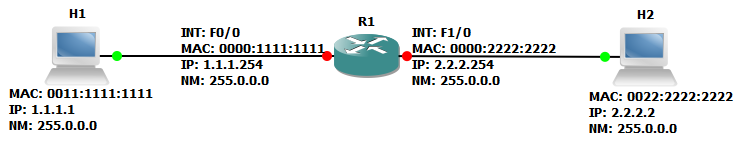
Let’s check how host H1 can communicate with H2 from the figure 1.3. Before drilling into the details we must have a basic understanding the following terms: ARP, IP, and ICMP.
Figure 1.3 Hosts inside a Broadcast Domain.
ARP (Address Resolution Protocol): This is a Layer 2 protocol designed to map a Layer 3 address to a Layer 2 address. That means to map an IP address to its corresponding MAC address. For this the ARP protocol sends out a Layer 2 Broadcast with a single question “who has IP address X, please answer me with your MAC address”. When a host exists in the local Broadcast Domain with the IP address in question that host will answer to the ARP Request with its MAC address. The ARP request is off course destined to FFFF:FFFF:FFFF, the Layer 2 Broadcast address because the sender does not know the Layer 2 address of the IP address in question. The ARP Response will be a unicast because the receiver can read from the Frame the senders Layer 2 Address.
IP (Internet Protocol): IP protocol is designed to move data from H1 to H2 over the Internetwork. This is the first protocol of the OSI to provide end to end connectivity. The prime function is to find a way to get through to the destination in question. Every IP devices use a table to find a path to the given destination which is referred as Routing Table or Routing Information Base (RIB).
IP is also used as an addressing scheme at the Layer 3 of OSI. A group of Hosts in one room form one IP Network. Each Broadcast Domain must have its own IP Network and it must be unique in a given Internetwork. A 32bit IP address is divided into 2 parts, the network part and host part. Network part can be compared to a group of hosts in a single room which all have their room number (Network ID) identical and the host part is the individual unique number assigned to each hosts.
ICMP (Internet Control Message Protocol): This is an inbuilt protocol in the IP stack for diagnostic purposes. Ping is a diagnostic tool which sends ICMP messages to detect reachability in IP Networks. There are several message types for example ICMP request is message type 8 and Reply is type 0. A router on the path may not have a route in its routing table to the destination in question, thus will it send a destination network unreachable ICMP message to the source of the packet. This is a type 3 message and has code 0.
Now let us have a look at the actual communication process between the hosts. Let us assume that H2 initiates an ICMP request to H1.
1. H2 has to find out if the destination IP (H1) is in the same Network. For this H2 does a logical “AND” operation against the Destination IP address and the Local Network Mask, then it finds that H1 is in same Broadcast Domain.
2. H2 sends an ARP broadcast for the MAC address of H1.
3. H1 answers and now both of the hosts know the L2 addresses.
4. H2 encapsulates the ICMP Packet in a Frame and sends it to the Layer 2 destination address of H1.
5. H1 now replies the ICMP Request from H2 with an ICMP Reply.
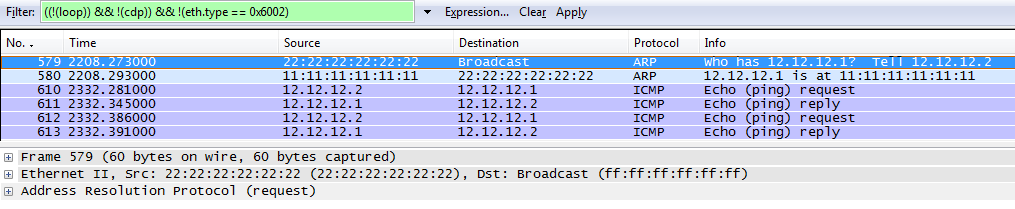
Figure 1.4 ARP Process.
The above figure 1.4 is a Wireshark capture of the communication flow. The ARP broadcast from H2 is highlighted. In the following frame you can see that H1 Replies for that ARP Request with its MAC address to H2. Since now H2 knows the Layer 2 address from H1 (MAC) it can encapsulate the ICMP Packet in the Frame and send to over the wire to H1.
Communication between hosts in different Broadcast Domains:
Let’s check how host H1 and H2 from figure 1.5, which resides in different Broadcast Domains communicate.
Figure 1.5 Hosts in different Broadcast Domains.
Again the same scenario, H2 sends an ICMP echo request to H1. The difference in this case as you see in the topology is that we are having 2 Broadcast Domains. Let us walk through the process.
1. H2 has to find out if the destination IP (H2) is in the same Network. For this H2 does a logical “AND” operation against the Destination IP address and the Local Network Mask, thus it finds that H1 is NOT in the same Broadcast Domain.
2. H2 then checks if it has a Gateway configured (default route). Let’s assume that IP address of the interface f1/0 from R1 is configured as the Gateway.
3. Now H2 has to find the MAC address of the Gateway, so it ARPs for it.
4. Eventually H2 encapsulates the ICMP Packet in a Frame and sends it to the Layer 2 address of interface f1/0 from R1.
5. R1 does a routing lookup for the destination IP Network in the Routing Table (RIB) and it finds out that the packet can be forwarded out of interface f0/0.
6. Now again R1 has to find the Layer 2 address of H1, so that it can encapsulate the ICMP packet from H2 in the Frame destined to H1. So it ARPs for the L2 address of H1.
7. Thus when finally the echo request packet arrives at H1, it has to do the same things to get the reply back to H1.
The layer 2 Addressing is only valid inside a given Broadcast Domain. On the contrary Layer 3 address remains the same from start to end of the communication flow. The Broadcasts rate can be lowered by decreasing the size of the Broadcast Domain.
The Cisco Three-Layer Hierarchical Model:
Figure 1.6 Cisco Three-Layer model.
The Cisco hierarchical model can help you design, implement, and maintain a scalable, reliable, cost-effective hierarchical internetwork. Cisco defines three layers of hierarchy, as shown in the above figure 1.6.
The following are the three layers and their typical functions:
o The core layer: High speed data transfer
o The distribution layer: Routing of Packets
o The access layer: Delivering data to hosts
The Core Layer: The core layer is literally the core of the network. At the top of the hierarchy, the core layer is responsible for transporting large amounts of traffic both reliably and quickly. The only purpose of the network’s core layer is to switch traffic as fast as possible. The traffic transported across the core is common to a majority of users. If there is a failure in the core, every single user can be affected. Therefore, fault tolerance at this layer is an issue. The core is likely to see large volumes of traffic, so speed and latency are driving concerns here.
The Distribution Layer: The distribution layer is sometimes referred to as the workgroup layer and is the communication point between the access layer and the core. The primary functions of the distribution layer are to provide routing, filtering, and WAN access and to determine how packets can access the core, if needed. The distribution layer must determine the fastest way that network service requests are handled—for example, how a file request is forwarded to a server. After the distribution layer determines the best path, it forwards the request to the core layer if needed. The core layer then quickly transports the request to the correct service. The distribution layer is the place to implement policies for the network.
The Access Layer: The access layer controls user and workgroup access to internetwork resources. The access layer is sometimes referred to as the desktop layer. The network resources most users need will be available locally. The distribution layer handles any traffic for remote services.