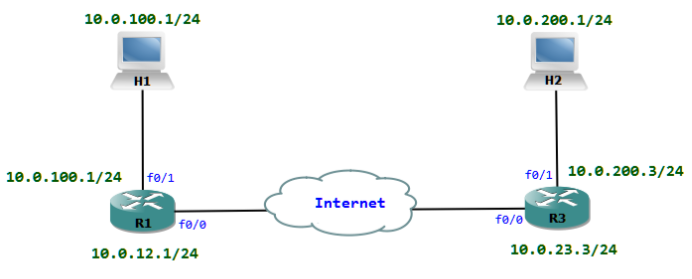
All communication between H1 and H2 must be protected with IPsec.
Tasks to do
- Classify interesting traffic
- Create ISAKMP policy and shared key for Phase 1
- Create IPsec Transform set for Phase 2
- Create a crypto map and apply crypto map to interface
Step 1: The Traffic which has to be protected with IPsec must be classified with an ACL. We can now create an ACL which matches packets between the 10.0.100.0/24 and 10.0.200.0/24 networks.
R1(config)#ip access-list extended PROTECTED_TRAFFIC
R1(config-ext-nacl)# permit ip 10.0.100.0 0.0.0.255 10.0.200.0 0.0.0.255
Step 2: We have to create an ISAKMP Policy for the Phase 1. Here we define the DH group, encryption algorithm, authentication method, hashing method etc. There could be many policies configured, only the matching policy one on both sides will be used.
R1(config)#crypto isakmp policy 10
R1(config-isakmp)# encryption aes
R1(config-isakmp)# authentication pre-share
R1(config-isakmp)# group 2
As we are using a shared key for authentication, we have to define it.
R1(config)#crypto isakmp key cisco address 10.0.23.3
Step 3: Now we can configure the Transform set for IKE Phase 2. There could be many policies for Phase 2 transform set. When the routers find a match they use that particular transform set.
R1(config)#crypto ipsec transform-set TRANS1 esp-aes esp-sha-hmac
Step 4: Finally we can create a crypto map and apply it to an interface. A crypto map combines the ACL with the Transform set. Then at last the crypto map is applied to the interface.
R1(config)#crypto map INT_F0/0 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
R1(config-crypto-map)# set peer 10.0.23.3
R1(config-crypto-map)# set transform-set TRANS1
R1(config-crypto-map)# match address PROTECTED_TRAFFIC
R1(config-crypto-map)#exit
R1(config)#interface FastEthernet0/0
R1(config-if)# ip address 10.0.12.1 255.255.255.0
R1(config-if)# crypto map INT_F0/0
%CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
R1(config-if)#end
We could verify the status of the security associations. We could also see the packets which are protected with IPsec. The state QM_IDLE means Quick Mode is in idle which implies IPsec in operation.
R1#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
10.0.12.1 10.0.23.3 QM_IDLE 1003 0 ACTIVE
IPv6 Crypto ISAKMP SA
R1#sh crypto ipsec sa
interface: FastEthernet0/0
Crypto map tag: INT_F0/0, local addr 10.0.12.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.0.100.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.0.200.0/255.255.255.0/0/0)
current_peer 10.0.23.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 23, #pkts encrypt: 23, #pkts digest: 23
#pkts decaps: 26, #pkts decrypt: 26, #pkts verify: 26
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 3, #recv errors 0
local crypto endpt.: 10.0.12.1, remote crypto endpt.: 10.0.23.3
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0x0(0)
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas: