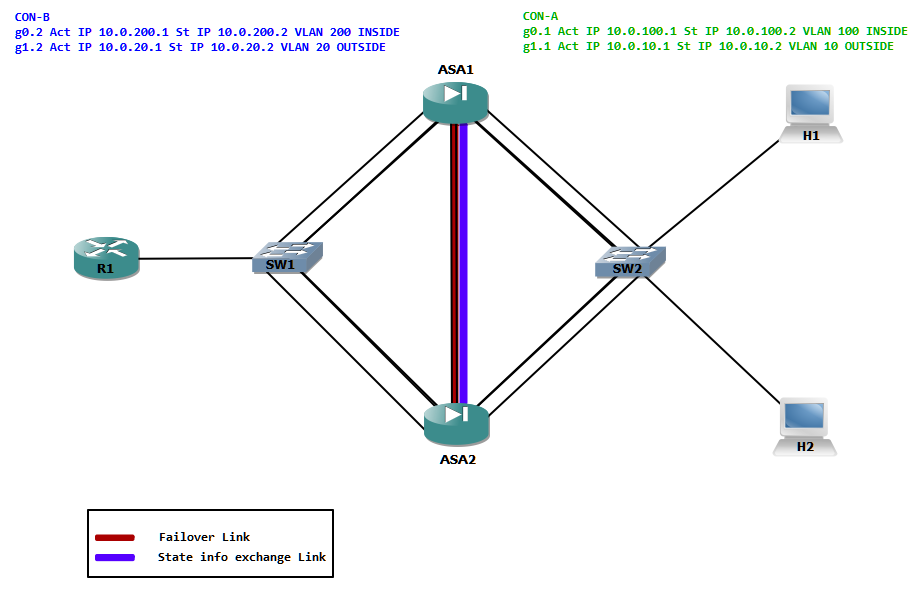
Task list
- Change the mode to multiple
- Context definition and assign interfaces
- Assign primary and secondary IP address
- Failover configuration
Step 1: First we have to change the default mode of single to multiple. A reboot is required. Only multiple mode supports contexts, which are needed to build virtual firewalls.
ASA1(config)# mode multiple
WARNING: This command will change the behavior of the device
WARNING: This command will initiate a Reboot
Proceed with change mode? [confirm]
Convert the system configuration? [confirm]
Step 2: Since the ASA is now in multiple context mode, we could define contexts named CON-A and CON-B. We must also provide the location of configuration file. Finally the interfaces should also be assigned. The interfaces must be un shut and if needed subinterfaces must be created at the system context.
ciscoasa# conf t
ciscoasa(config)# context CON-A
Creating context 'CON-A'... Done. (2)
ciscoasa(config-ctx)# config-url disk0:/con-a.cfg
WARNING: Could not fetch the URL disk0:/con-a.cfg
INFO: Creating context with default config
ciscoasa(config-ctx)# allocate-interface GigabitEthernet 0.100
ciscoasa(config-ctx)# allocate-interface GigabitEthernet 1.10
ciscoasa(config-ctx)# context CON-B
Creating context 'CON-B'... Done. (3)
ciscoasa(config-ctx)# config-url disk0:/con-b.cfg
WARNING: Could not fetch the URL disk0:/con-b.cfg
INFO: Creating context with default config
ciscoasa(config-ctx)# allocate-interface GigabitEthernet 0.200
ciscoasa(config-ctx)# allocate-interface GigabitEthernet 1.20
Step 3: Now we can assign IP address and nameif to the interfaces from the respective contexts. For that we have to change to each context. The primary IP address will be used by the active device from each context.
ciscoasa(config-ctx)# changeto context CON-A
ciscoasa/CON-A(config)# interface GigabitEthernet 0.100
ciscoasa/CON-A(config-if)# nameif INSIDE
INFO: Security level for "INSIDE" set to 100 by default.
ciscoasa/CON-A(config-if)# ip address 10.0.100.1 255.255.255.0 standby 10.0.100.2
ciscoasa/CON-A(config-if)# interface GigabitEthernet 0.10
ciscoasa/CON-A(config-if)# nameif OUTSIDE
INFO: Security level for "OUTSIDE" set to 0 by default.
ciscoasa/CON-A(config-if)# ip add 10.0.10.1 255.255.255.0 standby 10.0.10.2
ciscoasa/CON-A(config-if)# changeto context CON-B
ciscoasa/CON-B(config)# interface gigabitEthernet 1.20
ciscoasa/CON-B(config-if)# nameif OUTSIDE
INFO: Security level for "OUTSIDE" set to 0 by default.
ciscoasa/CON-B(config-if)# ip address 10.0.20.1 255.255.255.0 standby 10.0.20.2
ciscoasa/CON-B(config-if)# interface gigabitEthernet 0.200
ciscoasa/CON-B(config-if)# nameif INSIDE
INFO: Security level for "INSIDE" set to 100 by default.
ciscoasa/CON-B(config-if)# ip address 10.0.200.1 255.255.255.0 standby 10.0.200.2
Step 4: The failover configurations are made in the system context. ASA1 is defined as the primary unit. A failover interface for heart beats must also be defined. The failover interface is named FAILOVER and assigned primary and standby IP address. Another link is defined for the state information updates. The state information link is named STATE and also assigned IP address. Finally we define the primary and secondary groups. These groups are assigned to contexts. The last step is to enable failover.
ASA1/CON-B(config-if)# changeto system
ASA1(config)# failover lan unit primary
ASA1(config)# failover lan interface FAILOVER GigabitEthernet5
ASA1(config)# failover link STATE GigabitEthernet4
ASA1(config)# failover interface ip FAILOVER 10.0.0.1 255.255.255.0 standby 10.0.0.2
ASA1(config)# failover interface ip STATE 10.0.1.1 255.255.255.0 standby 10.0.1.2
ASA1(config)# failover group 1
ASA1(config-fover-group)# primary
ASA1(config-fover-group)# failover group 2
ASA1(config-fover-group)# secondary
ASA1(config-fover-group)# context CON-A
ASA1(config-ctx)# join-failover-group 1
ASA1(config-ctx)# context CON-B
ASA1(config-ctx)# join-failover-group 2
ASA1(config-ctx)# failover
On the ASA2 we just have to define the unit as secondary, assign an interface for failover and enable failover.
ASA2(config)# failover lan unit secondary
ASA2(config)# failover lan interface FAILOVER GigabitEthernet5
INFO: Non-failover interface config is cleared on GigabitEthernet5 and its sub-interfaces
ASA2(config)# failover interface ip FAILOVER 10.0.0.1 255.255.255.0 standby 10.0.0.2
ASA2(config)# failover
For clarity we could change the prompt to display which firewall is active. The default prompt consists of hostname and context. We could add priority and state which gives a better view of at which device we are consoled to.
ASA1# conf t
ASA1(config)# prompt hostname context priority state
ASA1/pri/act(config)# end
We could verify the failover state with the command show failover. The output shows that this firewall is active the group 1 and in standby for group 2.
ASA1/pri/act# show failover
Failover On
Failover unit Primary
Failover LAN Interface: FAILOVER GigabitEthernet5 (up)
Unit Poll frequency 1 seconds, holdtime 15 seconds
Interface Poll frequency 5 seconds, holdtime 25 seconds
Interface Policy 1
Monitored Interfaces 4 of 60 maximum
Version: Ours 8.4(2), Mate 8.4(2)
Group 1 last failover at: 17:25:07 UTC May 12 2012
Group 2 last failover at: 17:10:04 UTC May 12 2012
This host: Primary
Group 1 State: Active
Active time: 348 (sec)
Group 2 State: Standby Ready
Active time: 0 (sec)
CON-A Interface INSIDE (10.0.100.1): Normal (Monitored)
CON-A Interface OUTSIDE (10.0.10.1): Normal (Monitored)
CON-B Interface INSIDE (10.0.200.2): Normal (Monitored)
CON-B Interface OUTSIDE (10.0.20.2): Normal (Monitored)
Other host: Secondary
Group 1 State: Standby Ready
Active time: 1048 (sec)
Group 2 State: Active
Active time: 1396 (sec)
CON-A Interface INSIDE (10.0.100.2): Normal (Monitored)
CON-A Interface OUTSIDE (10.0.10.2): Normal (Monitored)
CON-B Interface INSIDE (10.0.200.1): Normal (Monitored)
CON-B Interface OUTSIDE (10.0.20.1): Normal (Monitored)
Stateful Failover Logical Update Statistics
Link : STATE GigabitEthernet4 (up)
Stateful Obj xmit xerr rcv rerr
General 166 0 169 0
sys cmd 166 0 166 0
up time 0 0 0 0
RPC services 0 0 0 0
TCP conn 0 0 0 0
UDP conn 0 0 0 0
ARP tbl 0 0 0 0
Xlate_Timeout 0 0 0 0
IPv6 ND tbl 0 0 0 0
SIP Session 0 0 0 0
Route Session 0 0 0 0
User-Identity 0 0 3 0
Logical Update Queue Information
Cur Max Total
Recv Q: 0 2 1416
Xmit Q: 0 1 166
ASA1/pri/act#