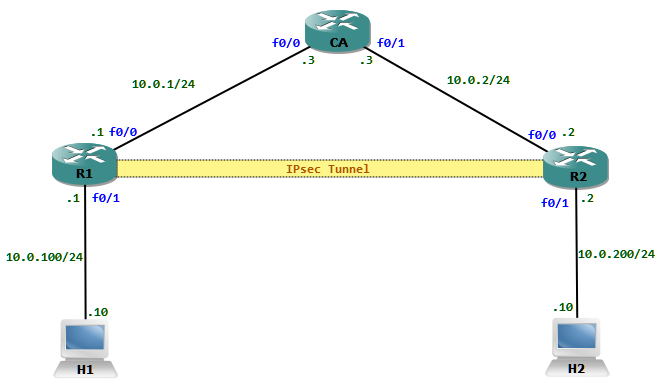
All communication between H1 and H2 must be protected with IPsec.
Tasks to do
- Synchronize the time
- Configure IOS CA Server
- Enroll routers to attain certificates
- Classify interesting traffic
- Configure ISAKMP Phase 1 policy and IPsec Phase 2 Transform set
- Create a crypto map and apply crypto map to interface
Step 1: Time must be synchronized for certificates to work properly. The CA router could be configured as a NTP master which then will provides time to other routers.
CA(config)#ntp master
The routers will be configured to get the time from the NTP master.
R1(config)#ntp server 10.0.1.3
R2(config)#ntp server 10.0.2.3
Step 2: The Certificate authority needs to be installed in the CA router. Http server must be enabled as we are going to auto enroll the clients via http. We name the CA as IOS_CA and enable it.
CA(config)#crypto pki server IOS_CA
CA(cs-server)#grant auto
May 12 23:25:30.567: %PKI-6-CS_GRANT_AUTO: All enrollment requests will be automatically granted.
CA(cs-server)#no shutdown
%Some server settings cannot be changed after CA certificate generation.
% Please enter a passphrase to protect the private key
% or type Return to exit
Password:
Re-enter password:
% Generating 1024 bit RSA keys, keys will be non-exportable...[OK]
% Exporting Certificate Server signing certificate and keys...
% Certificate Server enabled.
May 12 23:27:25.531: %SSH-5-ENABLED: SSH 1.99 has been enabled
May 12 23:27:26.163: %PKI-6-CS_ENABLED: Certificate server now enabled.
CA(cs-server)#
Step 3: the clients must enroll to the CA for a certificate. For this the routers must have a trust point established to the CA. Only then they can enroll for a certificate. The IP address must be also inserted in the certificates, which is needed for ISAKMP Phase 1.
R1(config)#crypto pki trustpoint IOS_CA
R1(ca-trustpoint)#enrollment url http://10.0.1.3
R1(ca-trustpoint)#ip-address 10.0.1.1
R1(ca-trustpoint)#revocation-check none
R1(ca-trustpoint)#rsakeypair R1 1024
R1(ca-trustpoint)#exit
Now we can request for the certificate. First we have to authenticate and accept the server certificate.
R1(config)#crypto pki authenticate IOS_CA
Certificate has the following attributes:
Fingerprint MD5: D4C1BB0A BE5CA0D8 35CEC686 525483F5
Fingerprint SHA1: 69142011 B1C462DC C8027DE6 E7F10696 03168134
% Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
since we have the CA Certificate, we can enroll a certificate from the CA
R1(config)#crypto pki enroll IOS_CA
%
% Start certificate enrollment ..
% Create a challenge password. You will need to verbally provide this
password to the CA Administrator in order to revoke your certificate.
For security reasons your password will not be saved in the configuration.
Please make a note of it.
Password:
May 12 23:41:50.590: %SSH-5-ENABLED: SSH 1.99 has been enabled
May 12 23:41:50.594: %CRYPTO-6-AUTOGEN: Generated new 1024 bit key pair
Re-enter password:
% The subject name in the certificate will include: R1
% Include the router serial number in the subject name? [yes/no]: no
% The IP address in the certificate is 10.0.1.1
Request certificate from CA? [yes/no]: yes
% Certificate request sent to Certificate Authority
% The 'show crypto ca certificate IOS_CA verbose' commandwill show the fingerprint.
May 12 23:42:30.994: CRYPTO_PKI: Certificate Request Fingerprint MD5: B7F729ED 9A750E1F 3CD82197 B25A2470
May 12 23:42:30.994: CRYPTO_PKI: Certificate Request Fingerprint SHA1: CD7F6313 06E48032 39680976 CD8BBEDD 13A28129
May 12 23:42:31.702: %PKI-6-CERTRET: Certificate received from Certificate Authority
R1(config)#
Step 4: The Traffic which has to be protected with IPsec must be classified with an ACL. We can now create an ACL which matches packets between the 10.0.100.0/24 and 10.0.200.0/24 networks.
R1(config)#ip access-list extended PROTECTED_TRAFFIC
R1(config-ext-nacl)# permit ip 10.0.100.0 0.0.0.255 10.0.200.0 0.0.0.255
Step 5: We have to create an ISAKMP Policy for the Phase 1. Here we define the DH group, encryption algorithm, authentication method, hashing method etc. There could be many policies configured, only the matching policy one on both sides will be used.
R1(config)#crypto isakmp policy 10
R1(config-isakmp)# encryption aes
R1(config-isakmp)# group 5
Next we can configure the Transform set for IKE Phase 2. There could be many policies for Phase 2 transform set. When the routers find a match they use that particular transform set.
R1(config)#crypto ipsec transform-set TRANSFORM1 esp-aes esp-sha-hmac
Step 5: Finally a crypto map can be created and applied to the interface.
R1(config)#crypto map R2_MAP 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
R1(config-crypto-map)# set peer 10.0.2.2
R1(config-crypto-map)# set transform-set TRANSFORM1
R1(config-crypto-map)# match address PROTECTED_TRAFFIC
R1(config-crypto-map)#exit
R1(config)#interface fastEthernet 0/0
R1(config-if)#crypto map R2_MAP
May 12 23:59:03.648: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
R1(config-if)#end
We can verify the packets being encrypted
R1#sh cry ipsec sa
interface: FastEthernet0/0
Crypto map tag: R2_MAP, local addr 10.0.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.0.100.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.0.200.0/255.255.255.0/0/0)
current_peer 10.0.2.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 7, #pkts encrypt: 7, #pkts digest: 7
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 10.0.1.1, remote crypto endpt.: 10.0.2.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0xDC0ABBB8(3691690936)
inbound esp sas:
spi: 0x46376599(1178035609)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, crypto map: R2_MAP
sa timing: remaining key lifetime (k/sec): (4550720/3538)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xDC0ABBB8(3691690936)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, crypto map: R2_MAP
sa timing: remaining key lifetime (k/sec): (4550719/3538)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas: